The Attack Doesn’t Target Your Systems. It Targets Your People.
of cyber attacks involve social engineering
average cost of a social engineering breach
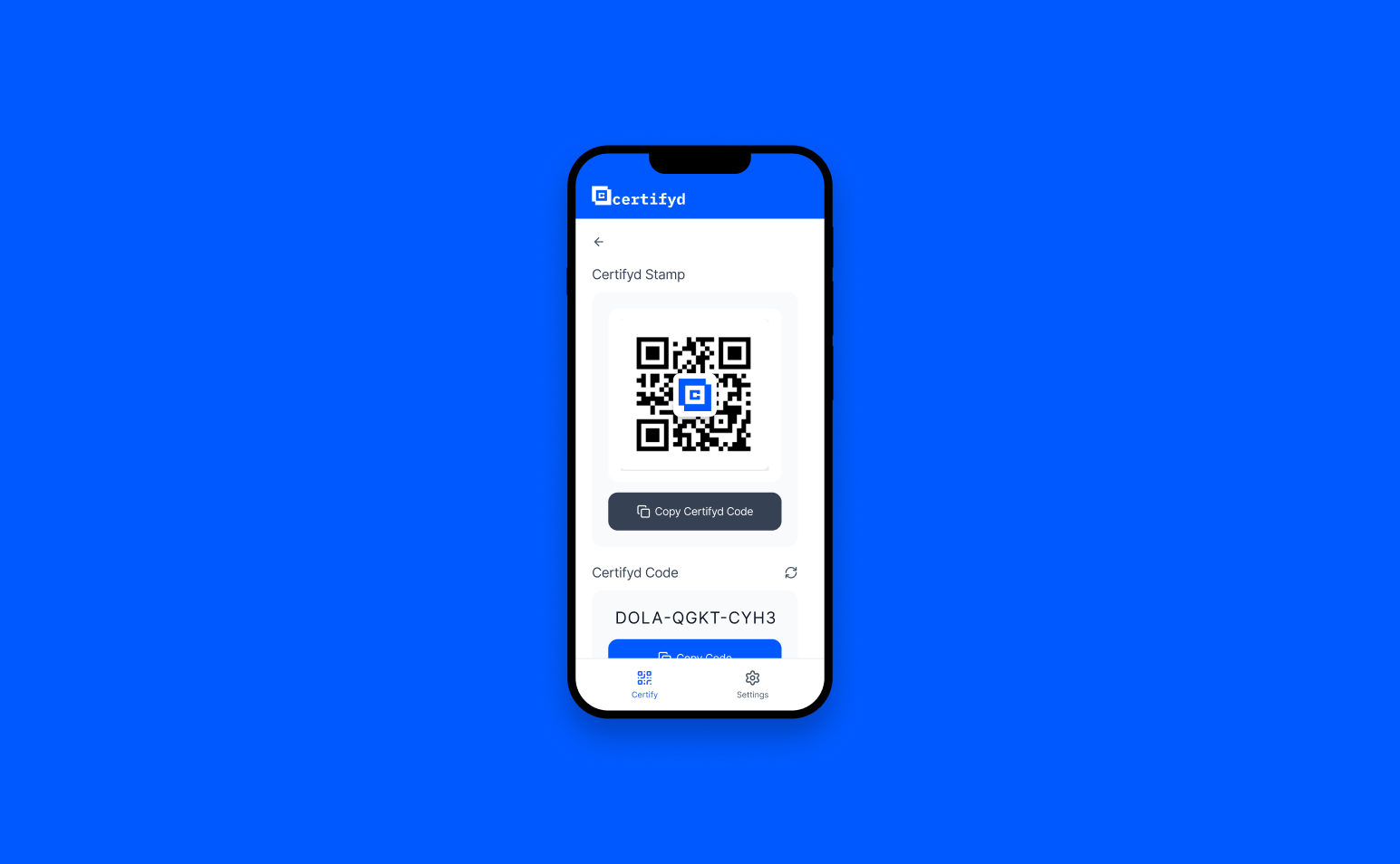
to verify with Certifyd
The reality of social engineering in the UK.
Social engineering protection with Certifyd addresses the fundamental vulnerability in all social engineering attacks: unverified identity. Whether the attacker impersonates a colleague, a vendor, IT support, or a bank official, the attack depends on the target trusting the attacker’s claimed identity. Certifyd provides a universal verification step: before acting on any request, the target can ask the requester to verify through device-bound cryptographic authentication. This transforms social engineering from a human judgement problem into a protocol problem — and protocols don’t get fooled.
98% of cyber attacks involve some form of social engineering. Not because social engineering is sophisticated, but because it’s reliable. Technical defences have improved dramatically — firewalls, encryption, multi-factor authentication. Social engineering bypasses all of them by targeting the human, not the system. An attacker who convinces an employee to share credentials doesn’t need to crack the encryption.
AI has made social engineering dramatically more effective. Attackers use large language models to craft contextually appropriate messages, voice cloning to impersonate known contacts, and deepfakes to conduct convincing video calls. The ‘human firewall’ approach — training employees to spot social engineering — is failing against AI-enhanced attacks because the attacks no longer exhibit the traditional red flags.
Certifyd addresses social engineering at the protocol level, not the perception level. Instead of training people to spot fakes (a losing battle), Certifyd provides a verification step that cannot be circumvented by social manipulation. When someone requests action, the target asks them to verify through their device-bound passkey. A social engineer cannot complete this challenge because they don’t possess the impersonated person’s physical device. Simple, fast, and unforgeable.
This is broken.
Here's why.
Social engineering bypasses every technical security control by targeting humans directly.
AI-enhanced attacks are too sophisticated for awareness training to reliably detect.
Impersonation of colleagues, executives, and trusted vendors exploits organisational trust.
The ‘human firewall’ approach fails when attackers can perfectly mimic the people employees trust.
Simple verification.
Every time.
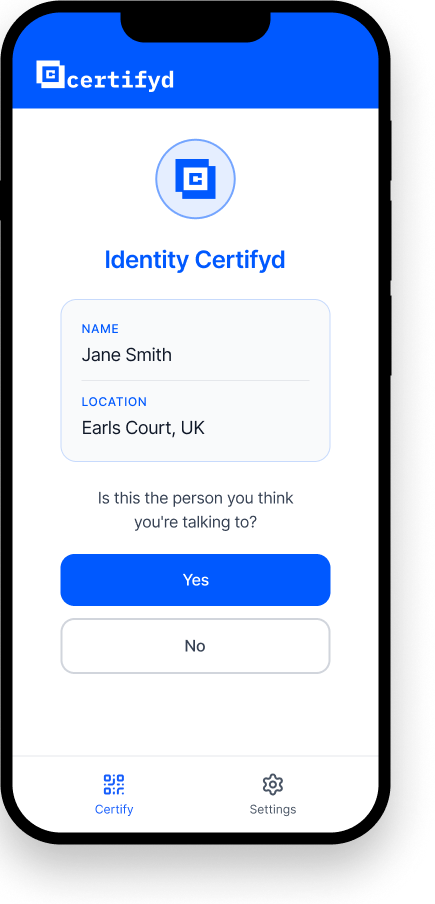
Employee receives a request from someone claiming to be a colleague, vendor, or authority figure
Employee asks the requester to verify through Certifyd — a 30-second device-bound authentication
The requester must complete a passkey challenge on their registered device
If they can’t complete it, the request is flagged as social engineering — before any action is taken
Ready to see it in action?
Book a demo or tell us about your needs.
“They created a voice model of his voice from public recordings. It sounded a bit like him, but knowing him well enough, I knew it wasn’t him. Most people wouldn’t.”— Cybersecurity professional, 20 years experience
Common questions.
Training improves awareness, but even trained employees fall for well-crafted social engineering 10–15% of the time. AI has raised the quality of attacks beyond what human perception can reliably detect. Voice cloning, deepfake video, and contextually perfect emails eliminate the traditional red flags that training teaches people to spot. The solution isn’t better training — it’s a protocol that removes the need for human judgement about identity.
Social engineering works because the attacker controls the narrative: they choose who to impersonate, what to request, and how to create urgency. Certifyd shifts control to the target. By requesting device-bound verification, the target introduces a step the attacker cannot fake. The attacker’s narrative, persuasion skills, and AI tools become irrelevant — they either have the real person’s device or they don’t. It turns social engineering from a human judgement problem into a binary verification outcome.
Certifyd works for in-person social engineering too. If someone claims to be a vendor, IT engineer, or auditor and requests physical access, the site manager can ask them to verify through Certifyd. The person must prove their identity and organisational membership through their device-bound passkey. Someone who tailgated through a secure entrance or is impersonating a vendor cannot complete this verification.
Yes. Supply chain attacks often involve impersonating a vendor to gain access or redirect payments. If a ‘vendor’ contacts you requesting a change to payment details or access credentials, requesting Certifyd verification confirms whether they are genuinely from the vendor organisation. Their device-bound identity is linked to their active organisational membership — an impersonator from outside the organisation cannot complete the verification.
Explore more use cases.
Related Solutions
External Resources
Protect your team from identity-based attacks
Book a demo to see how Certifyd works for your team, or tell us about your verification needs and we'll get back to you within 24 hours.
Read: The Deepfake Playbook