The Email Looks Right. The Sender Isn’t.
of UK businesses experienced phishing in 2024
average cost of a data breach (IBM, 2024)
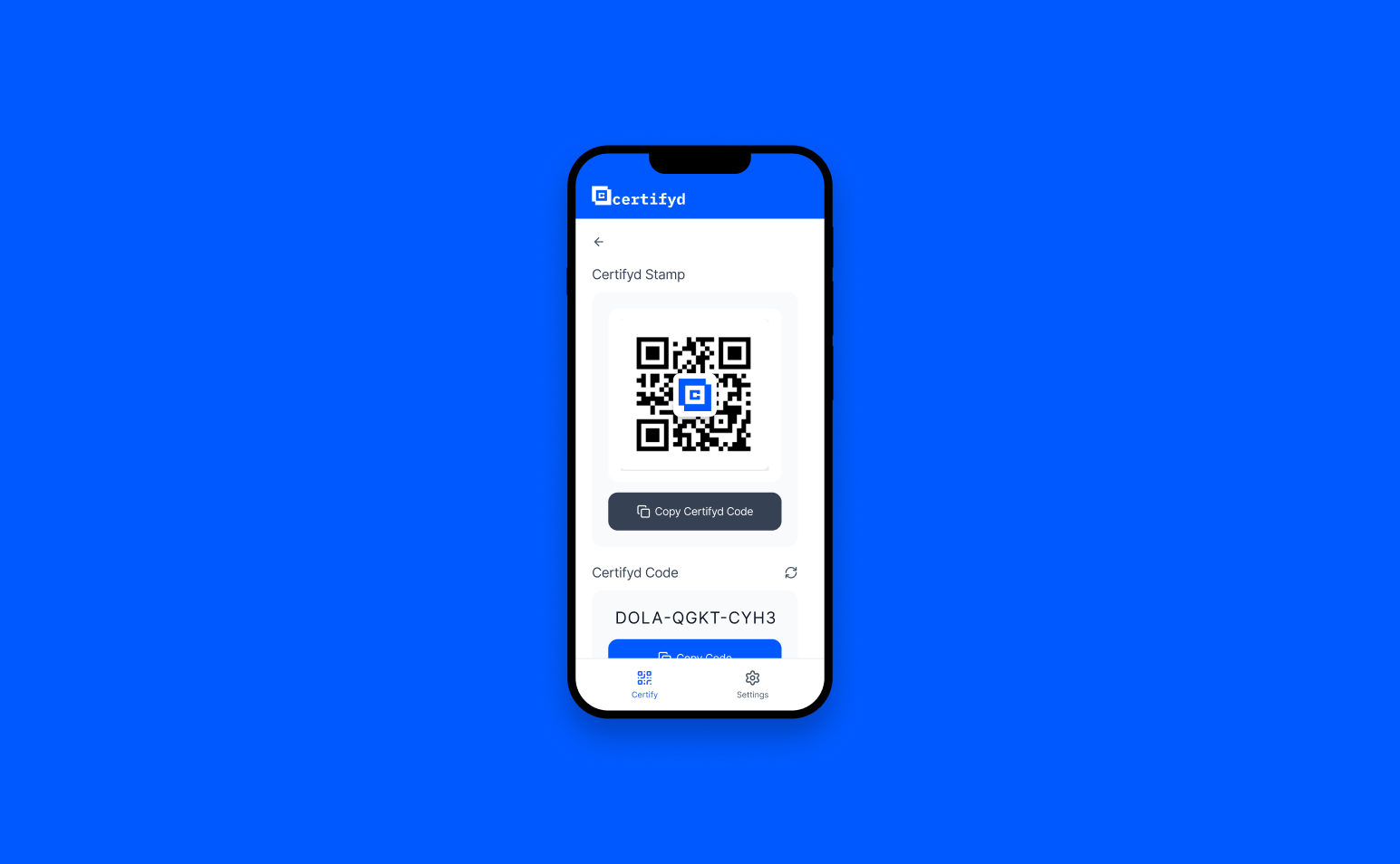
to verify with Certifyd
The reality of phishing in the UK.
Phishing protection with Certifyd adds cryptographic identity verification to communications where impersonation is the attack vector. Phishing succeeds because emails, messages, and calls can be made to appear to come from trusted sources. Certifyd doesn’t try to detect phishing — it lets the recipient verify the sender’s identity through device-bound authentication. Before acting on a suspicious request, the recipient asks the sender to complete a Certifyd verification. If they can’t — because they’re an impersonator — the attack fails.
83% of UK businesses experienced a phishing attack in 2024. Phishing remains the most common cyber attack vector because it exploits trust, not technology. An email that appears to come from a colleague, a text from the CEO, a call from IT — all can be impersonated with enough sophistication. Phishing awareness training helps, but even trained employees click on well-crafted phishing emails at rates of 10–15%.
AI has transformed phishing from a numbers game into a precision weapon. Large language models generate contextually appropriate emails that mirror the target’s communication style. Spear phishing campaigns research their targets through LinkedIn and social media. When the phishing email references a real project, uses the right internal terminology, and arrives at a plausible time — even cautious employees can be deceived.
Email security tools filter known phishing patterns, but novel attacks slip through. Certifyd provides a last line of defence: when an employee receives a suspicious request, they can verify the sender’s identity through Certifyd before acting. The sender must complete a device-bound passkey challenge. A phisher impersonating a colleague cannot complete this challenge because they don’t possess the colleague’s device. Simple, fast, and unforgeable.
This is broken.
Here's why.
Phishing emails have become indistinguishable from legitimate communications using AI.
Even trained employees fall for well-crafted spear phishing — awareness training has diminishing returns.
Email security tools catch known patterns but miss novel, targeted attacks.
The cost of a successful phishing attack (£4.4M average data breach) far exceeds the cost of prevention.
Simple verification.
Every time.
Employee receives a suspicious email or message requesting action
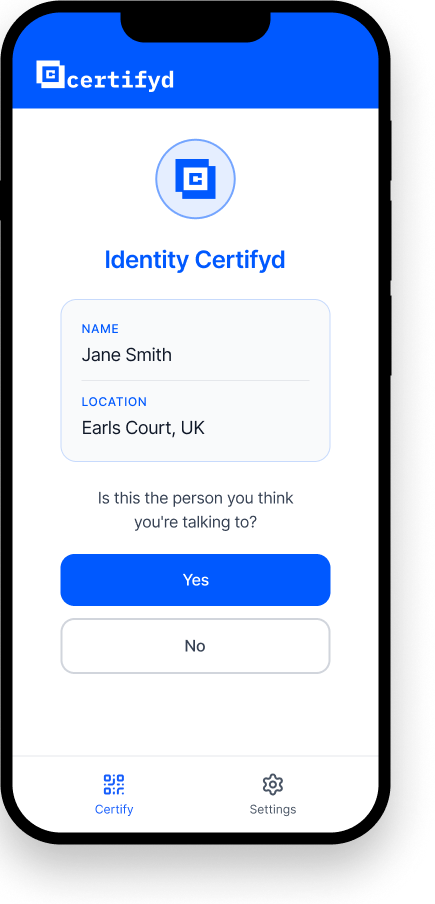
Employee asks the supposed sender to verify through Certifyd — a 30-second process
The sender completes a device-bound passkey challenge on their registered phone
If they can’t complete it, the message is confirmed as phishing — before any damage is done
Ready to see it in action?
Book a demo or tell us about your needs.
“When we hire somebody new, we get phishing attempts to them almost immediately. It’s always from the CEO saying ‘I’m in an important meeting, can you quickly do this?’”— Head of Cybersecurity, healthcare tech
Common questions.
Email security tools analyse emails for known phishing patterns — suspicious links, domain spoofing, attachment types. They’re valuable but reactive: they catch attacks that match known patterns. Certifyd adds sender identity verification: instead of analysing the email, it verifies the person who claims to have sent it. The sender must complete a cryptographic challenge on their registered device. This is proactive and defeats novel attacks that email filters haven’t seen before.
Certifyd verification takes 30 seconds and is only needed for suspicious or high-stakes communications. It’s not intended for every email — it’s a verification step for when something feels off or when the requested action has significant consequences. Think of it as a fire extinguisher: you don’t use it every day, but when you need it, it prevents catastrophic damage.
Voice phishing (vishing) is increasingly common, especially with voice cloning technology. Certifyd works across all channels: if someone calls claiming to be from IT, HR, or your bank, you can ask them to verify through Certifyd. The verification is device-bound, not channel-bound, so it works whether the impersonation attempt comes via email, phone, video call, or text message.
Certifyd verifies identity, which is the foundation of access control and authorisation. If someone within your organisation attempts to impersonate a more senior colleague (to authorise a payment, access restricted data, or approve a request), Certifyd verification will either confirm or refute their claimed identity. It protects against both external phishing and internal impersonation.
Explore more use cases.
Related Solutions
External Resources
Verify before you act on any request
Book a demo to see how Certifyd works for your team, or tell us about your verification needs and we'll get back to you within 24 hours.
Read: The Deepfake Playbook