The CEO Just Called. Or Did They?
UK CEO fraud losses (2023, Action Fraud)
of attacks use email or phone impersonation
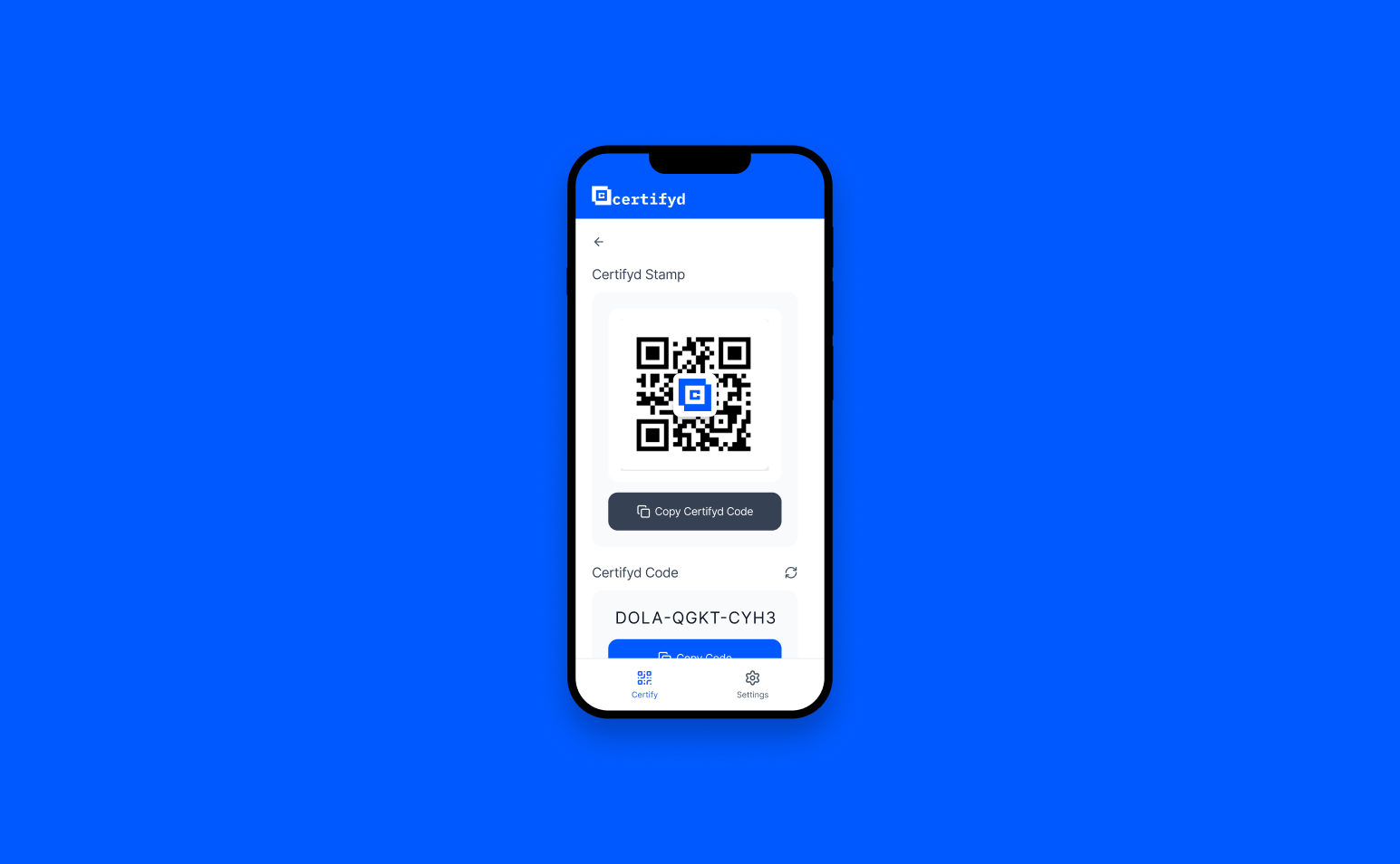
to verify with Certifyd
The reality of ceo fraud in the UK.
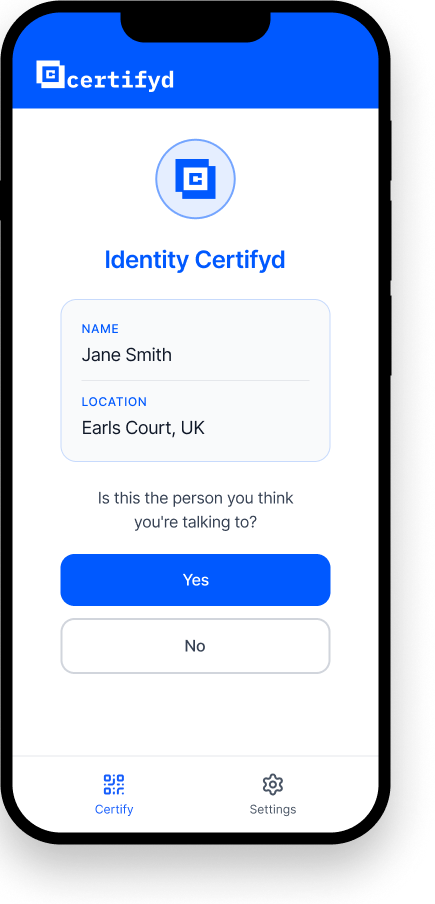
CEO fraud protection with Certifyd replaces trust in voices, emails, and video calls with cryptographic verification. Traditional CEO fraud relies on impersonating a senior executive — via email, phone, or increasingly via deepfake video. Certifyd defeats this by requiring device-bound authentication: before acting on any high-stakes instruction, the recipient can request that the supposed sender verify their identity through their registered device. A deepfake can clone a CEO’s voice and face, but it cannot complete a passkey challenge on the CEO’s phone.
CEO fraud — also known as business email compromise (BEC) or executive impersonation — costs UK businesses hundreds of millions annually. Action Fraud data shows losses of £245 million in 2023 alone. The attack vector is simple: a criminal impersonates a CEO, CFO, or other senior executive and instructs an employee to make an urgent payment, share credentials, or take some other high-stakes action.
The sophistication of these attacks has escalated dramatically. What used to be a poorly worded email is now a convincing voice call using cloned audio, or a deepfake video conference call (as in the Arup case). Criminals research targets thoroughly: they know the CEO’s communication style, their schedule, and their relationships. The urgency of the request (‘I’m in an important meeting, can you quickly do this?’) is designed to bypass verification procedures.
Training and awareness help, but they fail against high-quality impersonation. Certifyd provides a protocol-level solution: any employee receiving a high-stakes instruction can request the sender to verify through Certifyd. The sender must complete a passkey challenge on their registered device. If they can’t — because they’re not the real person — the instruction is flagged immediately. This makes CEO fraud structurally impossible, not just unlikely.
This is broken.
Here's why.
Deepfake voice and video calls can impersonate executives convincingly enough to authorise payments.
Email impersonation bypasses technical controls through social engineering, not technical exploits.
Employees are trained to be responsive to senior executives — urgency overrides verification instincts.
Existing controls (callback procedures, dual authorisation) fail when the attacker can clone the executive’s voice.
Simple verification.
Every time.
Employee receives a high-stakes instruction from a supposed executive
Employee requests the sender to verify through Certifyd — a 30-second device-bound authentication
If the sender is genuine, they complete the passkey challenge on their registered device
If they can’t complete it, the instruction is flagged as potentially fraudulent — crisis averted
Ready to see it in action?
Book a demo or tell us about your needs.
“When we hire somebody new, we get phishing attempts to them almost immediately. It’s always from the CEO saying ‘I’m in an important meeting, can you quickly do this?’”— Head of Cybersecurity, healthcare tech
Common questions.
Certifyd creates a verification step for high-stakes instructions. When an employee receives an unusual request from a supposed executive, they can ask the sender to verify through Certifyd. The sender must complete a cryptographic challenge on their registered device — something only the real executive possesses. A deepfake or impersonator cannot complete this challenge. The verification takes 30 seconds and creates a tamper-proof record.
Quite the opposite. CEOs who are serious about security will appreciate a team that verifies before acting on high-stakes requests. The alternative — losing £20 million to a deepfake because nobody wanted to question the boss — is far worse. Certifyd normalises verification as a professional standard, not a challenge to authority. Many organisations are making verification mandatory for payment authorisations above a threshold.
Even traditional email-based CEO fraud is defeated by Certifyd verification. If an employee receives an email that appears to come from the CEO, requesting a verification step through Certifyd means the attacker must possess the CEO’s physical device. Email spoofing, domain lookalikes, and compromised email accounts cannot complete a device-bound cryptographic challenge.
Yes. Certifyd verification can be incorporated into any high-stakes approval process. Before a payment is processed, the authoriser verifies through their device-bound passkey. This creates a tamper-proof record that the specific authorised person approved the specific transaction. It’s not just a signature or a login — it’s cryptographic proof that the real person, with the real device, authorised the action.
Explore more use cases.
Related Solutions
Related Reading
External Resources
Protect your business from executive impersonation
Book a demo to see how Certifyd works for your team, or tell us about your verification needs and we'll get back to you within 24 hours.
Read: The Arup Deepfake Attack